High Level Design
TEN is designed as an L2 protocol, where user activity is moved off-chain from the L1, and it follows the increasingly common rollup pattern to store transaction data on the L1 chain to achieve censorship-resistant data availability. This is leading to proposals to reduce calldata storage costs on Ethereum. Most rollup implementations exist to provide scalability for L1 networks, but the prime objective of TEN is to provide confidentiality. The rollups contain the entire encrypted transaction data.
L2 networks have a unidirectional dependency on an L1 network: while the L2 network relies on the L1 network to provide an immutable and public record of transaction data and to provide censorship resistance, liveness and availability, the L1 network is unaware of any individual L2 network. L2 submitted rollups are just normal L1 transactions.
The following diagram shows the interactions between the two decentralised networks, Ethereum (L1) and TEN (L2): TEN is formed of Nodes called Aggregators, who compete to process user transactions, roll them up, and submit for inclusion in Ethereum blocks. Ethereum, through its protocol, leverages its own nodes to produce Ethereum blocks containing, amongst other things, the submitted TEN rollups.
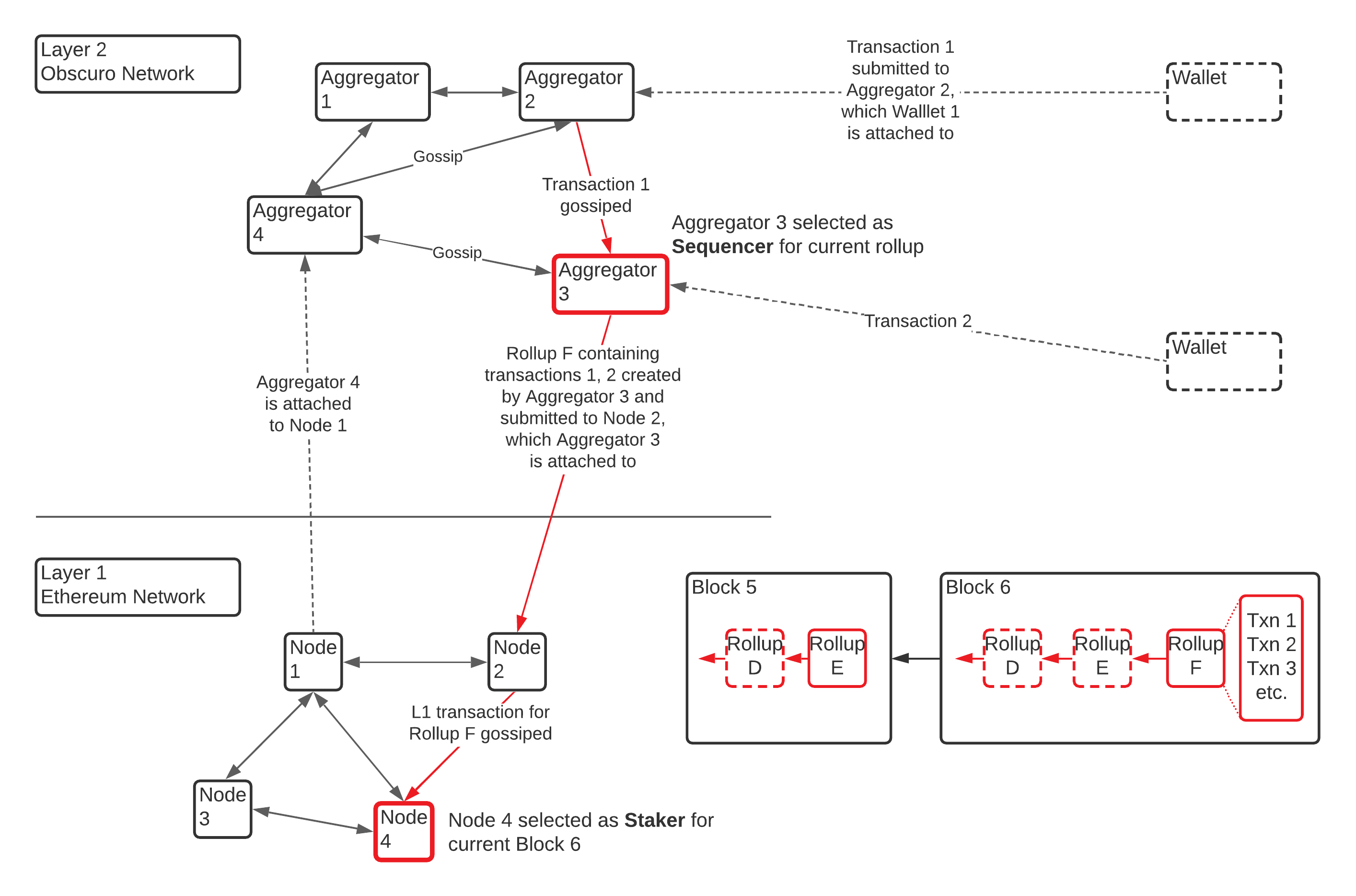
On the bottom right, this diagram also depicts the state of a simple rollup chain as it is found in the sequential L1 blocks.
L1 Network
On the L1 network there are several regular Ethereum contracts, referred to as Management Contracts.
Note: the L1 design is covered in more detail in L1 Contracts.
Network Management
This contract is the gatekeeper for the protocol. Any TEN node wishing to join the network will have to interact with this contract and prove it is valid. This contract will also manage the TEE attestation requirements and will be able to verify attestation reports.
It will also manage the stake of the participants able to submit rollups known as Aggregators.
Note: The stake is a piece of the game-theory puzzle that ensures that TEN participants have the right incentives to follow the protocol.
Rollup Management
This module accepts rollups submitted by L2 nodes and includes them in the rollup-chain structure. It works together with the bridge in processing withdrawal requests from users.
TEN Bridge
This contract is very important for the solution’s security since it will protect all liquidity deposited by Ethereum end-users, and reflected in the confidential TEN ledger.
L2 Network
The goal of the L2 design is to create a fair, permissionless, and decentralised network of nodes with valid TEEs who cannot see the transactions they are processing while collaborating to manage a ledger stored as rollups in the L1. The ledger should preserve its integrity even in the face of catastrophic TEE hacks.
All TEN nodes have to go through the attestation process with the Network Management contract before receiving the shared secret and participating.
Note: the shared secret is covered in the cryptography section.
L2 Nodes
There are two categories of nodes in the TEN network:
Aggregator Nodes
Aggregators are the TEN nodes whose TEEs are in possession of the shared secret and can submit rollups to the L1. To gain this privilege, these nodes must pledge a stake.
End users send encrypted transactions to any registered Aggregators who then gossip the transactions. Every round, one of the Aggregators publishes the transaction in a rollup.
Aggregators have the following functions:
- Integrate with an L1 node to monitor published blocks and to submit rollups.
- Gossip with the other aggregators registered in the Management Contract.
- Interact with the TEE module of the node:
- Submit user encrypted transactions.
- Submit signed user balance requests and encrypted responses back to the users.
- Submit proofs of block inclusion and receive signed rollups.
- Store data encrypted by the TEE and make it available when the TEE requests it. Act as an encrypted database.
Note that logically a node is split into two main sections:
- The section that is controlled by the node operator
- The TEE, which is attested to the Management contract and is in effect controlled by the governance body of TEN.
These are the steps to become an Aggregator.
- Register with the L1 Network Management contract and pay a significant stake in the TEN token. The stake has multiple roles. The first one is to penalise Aggregators who attempt to hack the protocol, and second is for the Aggregators to buy into the ecosystem, so that they will make an effort to keep it running smoothly.
- Set up a server with a valid, unaltered and up-to-date TEE and provide an attestation to the Management Contract.
- On seeing this request to join the network published to the L1, another registered TEE will share the shared secret.
- Once in possession of the secret, the TEE can start processing all the L2 transactions that are stored on the L1 blockchain and build the state.
- Once this is completed, the new Aggregator can join the gossip with the other Aggregators and participate in the lottery for producing rollups.
- Some end users will send encrypted instructions directly to this server, and it will gossip these with other nodes in the L2 network.
- As Aggregators process messages, they maintain the L2 state in the encrypted TEE memory and then journal encrypted data in a local database. If they are the winner of the round they can create a valid rollup and publish it to L1.
- All Aggregators keep track of the blocks submitted to the Management Contract to make sure they are up-to-date with the source of truth.
- The first Aggregator to register has a special role, as it has to create the Shared secret.
Note: Each Aggregator needs an ETH balance on the L1 to pay for the submission of the rollup.
The steps to register as an Aggregator are shown in the following diagram:
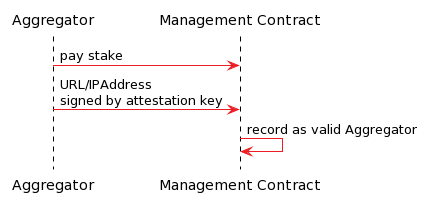
Verifier Nodes
Verifiers are TEE-equiped TEN nodes in possession of the shared secret and play a strong role in consensus security. They are configured differently and have not pledged the stake nor are they part of the Aggregator gossip network. To receive the L2 transactions, they monitor the L1 network and calculate the state based on the rollups submitted there.
End users can interact with either Aggregators or Verifiers to receive events on submitted transactions or query their accounts’ balance. Anyone can become a Verifier with minimal cost if they have compatible hardware.
Allowing these two categories lowers the bar for participation, thus making the network more robust and decentralised since more independent parties guard the shared secret and can react in the face of an attack.
Rollup Data Structure
The Management Contract implements a blockchain-like data structure to store the rollups. Each rollup points to a parent rollup, and at any time there can be multiple competing sibling rollups. Similar to L1 blockchains, it is the responsibility of the individual L2 nodes to decide which sibling is valid. The difference is that un-hacked nodes are running the same code and thus are not able to build upon an invalid rollup, or even to build on different rollups.
The diagram below depicts an L1 blockchain (in black). Each block contains a snapshot of the state of the TEN rollup chain (in Red). In this example, there are 5 TEN nodes.

Note that forks are possible on both layers, and it is the responsibility of the TEN nodes to navigate and choose the most likely L1 block. The following diagram depicts a couple of complex scenarios, where firstly an extra Aggregator publishes an additional rollup to a block, and secondly the L1 chain forks.
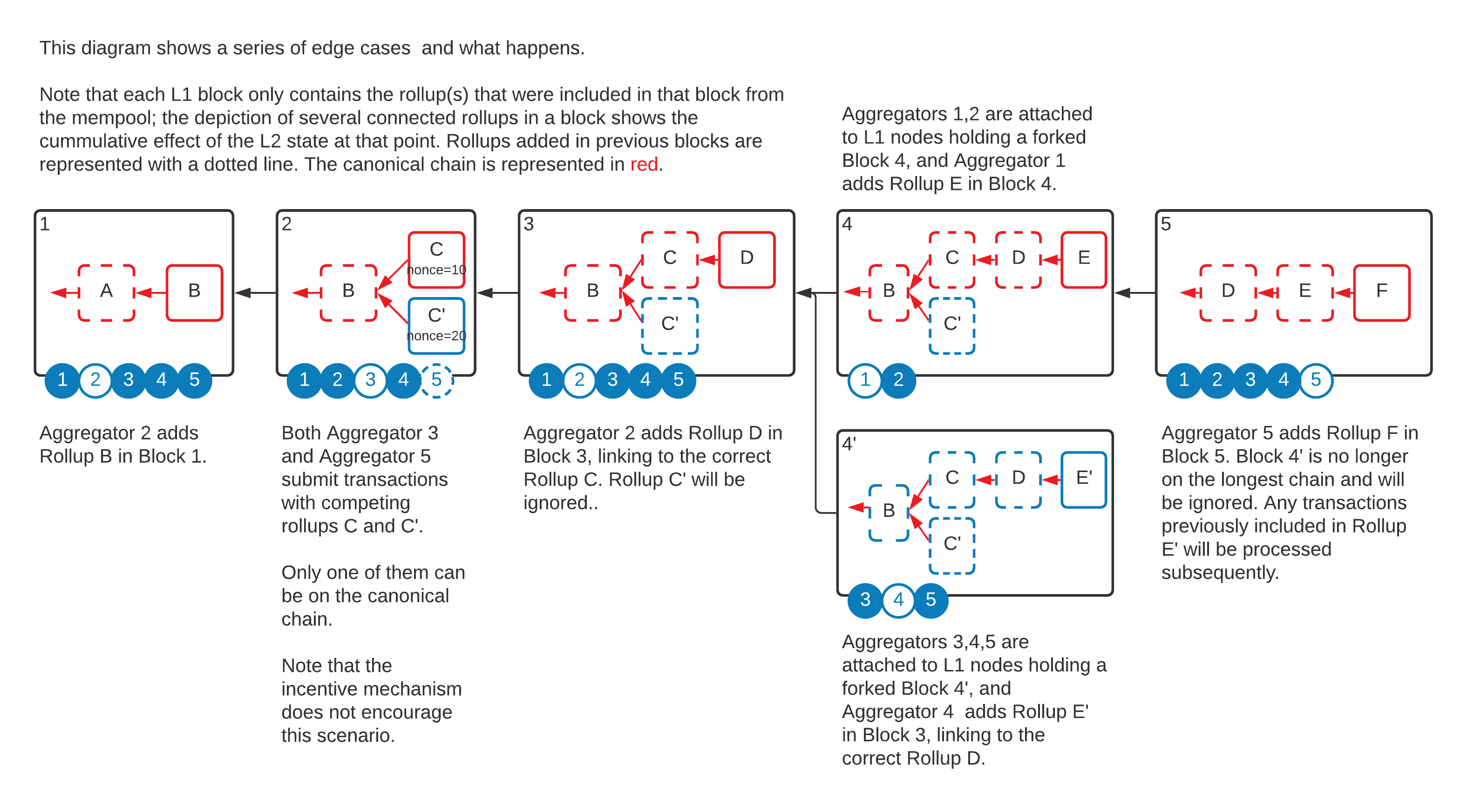
Note that this diagram will be dissected more after we introduce the consensus protocol. At this moment, it intends to give a high-level mental model of the decentralised nature of the L2 data model on top of the decentralised nature of the L1.